The Future- Hyper Convergence
Each Infra ( HCI ) architectures discussion start and end with limited business benefits that include:
- Ease of purchase
- Simple setup
- Consolidated management
- Full-stack support
- Pay-as-you-go economics
On the basis of my technical discussion with most of our customers, I have found that we are limiting our discussion at infrastructure level only. Although we all are aware that network security has became a key backbone for every business therefore there is a need to get on the ground and start asking about the current network architecture and its challenges. There are few major concerns which we need answers to , what are the current application blueprints, how users are accessing those applications and how secure is it?
We must involve Network – Application team into these discussions so that we will be able to get the visibility of our customer’s network and application which will enable us to provide complete solution to the customer.
I have personally experienced the difference in such meetings. I have found that customers are able to see the benefits and are getting clearer vision on solution and its benefits. They are now able to comprehend what is most more appropriate for them.
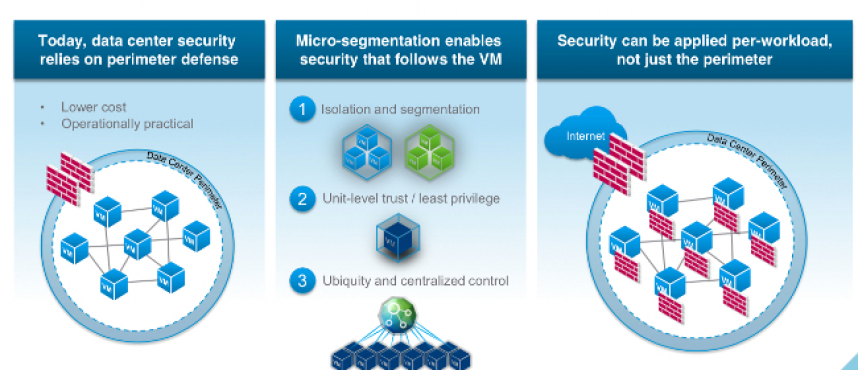
Micro-segmentation is a security technique that enables fine-grained security policies to be assigned to data center applications, down to the workload level. This approach enables security models to be deployed deep inside a data center, using a virtualized software-only approach. One major benefit of micro-segmentation is that it integrates security directly into a virtualized workload without requiring a hardware-based firewall. This means that security policies can be synchronized with a virtual network, virtual machine (VM), operating system (OS), or other virtual security targets. Security can be assigned down the level of a network interface, and the security policies can move with the VM or workload, in case of migration or reconfiguration of the network.
Disclaimer: The views presented here are personal opinions of the author and do not reflect the views of the organization. The author is basing these opinions on the experience that he has garnered over the past 20 years working in the information technology domain.